June 29, 2008 at 3:13 PM
—
2102
There is one little trick you need to remember if you are migrating VHDs with Vista/Server 2008 that was previously created on Virtual PC or Virtual Server 2005.
Enable Detect HAL!
How to Enable Detect HAL?
- Start the virtual machine and Run Msconfig.exe.
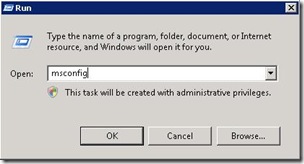
- In the System Configuration dialog box, click the Boot tab, and then click Advanced Options.
- In the BOOT Advanced Options dialog box, click to select the Detect HAL check box, and then click OK.
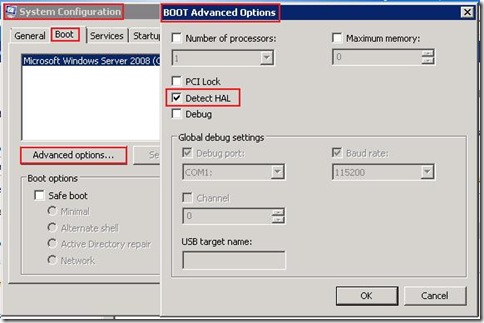
- Click Yes to restart the virtual machine.
- Clear the Detect HAL check box after reboot (it takes longer to boot).
Source: KB 954282 - The VMBus device does not load on a virtual machine that is running on a Windows Server 2008-based computer that has Hyper-V installed
September 4, 2007 at 2:06 PM
—
2102
After a Windows Vista-based computer has been running for an extended period of time, the desktop screen may stop updating correctly. For example, you may experience any of the following symptoms:
- Parts of the screen may go black.
- Parts of the screen may become transparent.
- The toolbar may disappear.
- The toolbar may appear at the top of the screen instead of at the bottom of the screen.
KB932406 - The Windows desktop may stop updating correctly after a Windows Vista-based computer has been running for an extended period of time
Now my problems with transparent or black parts of screen are gone. :)
August 20, 2007 at 8:41 AM
—
2102
Well... If you run Disk Cleanup and if you select Hibernation File Cleaner it will disable hibernation in Windows Vista.

To re-enable hibernation run this from command line. And don`t forget to run as Administrator :)
powercfg -H ON
To disable hibernation in Windows Vista run this from command line as Administrator.
powercfg -H OFF
June 28, 2006 at 11:38 AM
—
2102
These step-by-step guides provide instructions for deploying or migrating to Windows Vista. These guides also describe how to configure security, monitor performance, and manage printers.
Overview
These step-by-step guides will assist IT Professionals in deploying or migrating to Windows Vista. These guides will also provide step-by-step information on how to control device installation using Device Management and Installation (DMI) and manage ADMX files. There are also step-by-step guides to help you protect data using BitLocker Drive Encryption, to administer the TPM Security Hardware in a computer using Trusted Platform Module (TPM) Services, and to help deploy better-managed desktops and mitigate the impact of malware using User Account Control (UAC).
Download: Windows Vista Step-by-Step Guides for IT Professionals v2.9
May 27, 2006 at 8:11 PM
—
2102
Today I spent some time playing arround Windows Vista Beta 2. There is one interesting thing that i found out. It has ASLR (Address Space Layout Randomization) and it is turned on by default. It is a great against defense against buffer overrrun exploits called address space layout randomization. This defense is of course not a replacement for insecure code but it is indeed a usefull in Mult-Llayered defense. So remote exploitation of overflows has just got a lot harder.
So what is ASLR?
Address space layout randomization (ASLR) is a computer security feature which involves arranging the positions of key data areas, usually including the base of the executable and position of libraries, heap, and stack, randomly in a process' address space. This hinders some types of security attack by preventing an attacker being able to easily predict target addresses, for example attackers trying to execute return-to-libc attacks may find it harder to locate the code to be executed. Several security systems implement ASLR, notably OpenBSD and the PaX and Exec Shield patches for Linux.
ASLR relies on the low chance of an attacker guessing where randomly placed areas are located: the odds are 1 / 2b, where b is the number of bits of entropy used to determine the position of the data area. In many systems, 2b can be in the thousands or millions; on modern 64-bit systems, these numbers typically reach the millions at least. Some systems implement Library Load Order Randomization, a form of ASLR where the order in which libraries are loaded is randomised. This leaves libraries at unpredictable positions: the chances of an attacker correctly guessing the location of a library is 1 / n, where n is the number of libraries loaded.