August 15, 2013 at 10:50 PM
—
Saso Erdeljanov
Microsoft temporary removed MS13-061 security update for Exchange Server 2013 due to bug with content index. After installation you will notice Content Index for mailbox databases failed and service Microsoft Exchange Search Host Controller service is renamed.
For customers that already deployed updated, Microsoft provided KB article with steps to resolve issue.
Update 2874216 breaks the content index in Exchange Server 2013
After you install update 2874216, you experience the following issues in Microsoft Exchange Server 2013:
The content index (CI) for mailbox databases shows "Failed" on the affected server.
The Microsoft Exchange Search Host Controller service is missing.
You see a new service that is named "Host Controller service for Exchange."
Links:
Update 2874216 breaks the content index in Exchange Server 2013
Exchange 2013 Security Update MS13-061 Status Update
August 13, 2013 at 8:08 PM
—
Saso Erdeljanov
Microsoft just released a bunch of updates for Microsoft Exchange Server 2007, Exchange Server 2010 and Exchange Server 2013. It’s important to deploy updates since they contain security fixes.
Update Rollup 11 for Exchange Server 2007 SP3
Update Rollup 7 for Exchange Server 2010 SP2
Update Rollup 2 for Exchange Server 2010 SP3
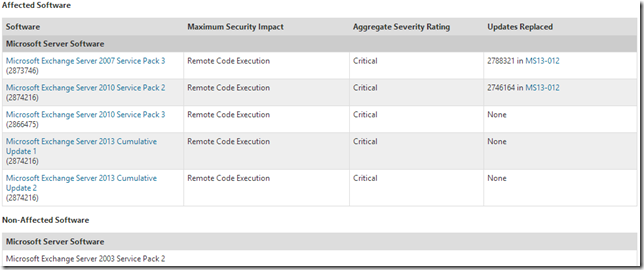
Exchange Server 2013 RTM CU1 MSRC Security bulletin MS13-061
Exchange Server 2013 RTM CU2 MSRC Security bulletin MS13-061
Microsoft Security Bulletin MS13-061 - Critical
Exchange 2007 Rollups
The Exchange 2007 SP3 RU11 update contains two fixes in addition to the changes for MS13-061. For more details, including a list of fixes included in this update, seeKB 2873746 and the MS13-061 security bulletin. We would like to specifically call out the following fixes which are included in this release:
- 2688667 W3wp.exe consumes excessive CPU resources on Exchange Client Access servers when users open recurring calendar items in mailboxes by using OWA or EWS
- 2852663 The last public folder database on Exchange 2007 cannot be removed after migrating to Exchange 2013
Exchange 2010 Rollups
The Exchange 2010 SP2 RU7 update contains the changes for MS13-061. For more details, see the MS13-061 security bulletin.
The Exchange 2010 SP3 RU2 update contains fixes for a number of customer-reported and internally found issues, as well as, the changes for MS13-061. For more details, including a list of fixes included in this update, see KB 2866475 and the MS13-061 security bulletin. We would like to specifically call out the following fixes which are included in this release:
- 2861118 W3wp.exe process for the MSExchangeSyncAppPool application pool crashes in an Exchange Server 2010 SP2 or SP3 environment
- 2851419 Slow performance in some databases after Exchange Server 2010 is running continuously for at least 23 days
- 2859596 Event ID 4999 when you use a disclaimer transport rule in an environment that has Update Rollup 1 for Exchange Server 2010 SP3 installed
- 2873477 All messages are stamped by MRM if a deletion tag in a retention policy is configured in an Exchange Server 2010 environment
- 2860037 iOS devices cannot synchronize mailboxes in an Exchange Server 2010 environment
- 2854564 Messaging Records Management 2.0 policy can't be applied in an Exchange Server 2010 environment
Exchange Server 2013
MS13-061 is the first security update released for Exchange Server 2013 utilizing the new servicing model. MS13-061 is available as a security update for:
Important: If you have previously deployed CU2, you must ensure you are running build 712.24 in order to apply the security update. For more information about build 712.24, please see Now Available: Updated Release of Exchange 2013 RTM CU2.
External links & downloads:
Update Rollup 11 for Exchange Server 2007 Service Pack 3 (KB2873746)
Update Rollup 7 for Exchange Server 2010 Service Pack 2 (KB2874216)
Update Rollup 2 For Exchange 2010 SP3 (KB2866475)
Security Update For Exchange Server 2013 CU1 (KB2874216)
Security Update For Exchange Server 2013 CU2 (KB2874216)
Released: Update Rollups for Exchange 2007 & Exchange 2010 and Security Updates for Exchange 2013
July 17, 2008 at 1:06 PM
—
2102
This update adds support for the following Advanced Encryption Standard (AES) cipher suites in the Schannel.dll module for Windows Server 2003:
- TLS_RSA_WITH_AES_128_CBC_SHA AES128-SHA
- TLS_RSA_WITH_AES_256_CBC_SHA AES256-SHA
Note: These cipher suites are based on the RC4 algorithm.
Source:
KB948963 - An update is available to adds support for the TLS_RSA_WITH_AES_128_CBC_SHA AES128-SHA and the TLS_RSA_WITH_AES_256_CBC_SHA AES256-SHA AES cipher suites in Windows Server 2003
September 1, 2007 at 11:52 AM
—
2102
Forefront Server Security Management Console allows administrators to easily manage Forefront Security for Exchange Server, Forefront Security for SharePoint and Microsoft Antigen, providing a web-based console to centralize configuration and operation, automate the download and distribution of signature and scan engine updates, and generate comprehensive reports. Forefront Server Security Management Console also allows administrators to rapidly respond to outbreaks and update protection across enterprise deployments, improving organizational agility in responding to new threats. Through integration with Windows Server 2003 and Microsoft SQL Server, Forefront Server Security Management Console helps maintain reliability and performance of messaging and collaboration protection.
Download it here.
August 11, 2007 at 9:07 AM
—
2102
What happens if you try to capture with hidden camera hackers admitting to crimes? What happens if you try this at DefCon? Nothing good I guess... Here is a video of Michelle Medigan from NBC News attempted to use a hidden camera at DefCon.
Here and here is complete story... :)
May 27, 2006 at 8:11 PM
—
2102
Today I spent some time playing arround Windows Vista Beta 2. There is one interesting thing that i found out. It has ASLR (Address Space Layout Randomization) and it is turned on by default. It is a great against defense against buffer overrrun exploits called address space layout randomization. This defense is of course not a replacement for insecure code but it is indeed a usefull in Mult-Llayered defense. So remote exploitation of overflows has just got a lot harder.
So what is ASLR?
Address space layout randomization (ASLR) is a computer security feature which involves arranging the positions of key data areas, usually including the base of the executable and position of libraries, heap, and stack, randomly in a process' address space. This hinders some types of security attack by preventing an attacker being able to easily predict target addresses, for example attackers trying to execute return-to-libc attacks may find it harder to locate the code to be executed. Several security systems implement ASLR, notably OpenBSD and the PaX and Exec Shield patches for Linux.
ASLR relies on the low chance of an attacker guessing where randomly placed areas are located: the odds are 1 / 2b, where b is the number of bits of entropy used to determine the position of the data area. In many systems, 2b can be in the thousands or millions; on modern 64-bit systems, these numbers typically reach the millions at least. Some systems implement Library Load Order Randomization, a form of ASLR where the order in which libraries are loaded is randomised. This leaves libraries at unpredictable positions: the chances of an attacker correctly guessing the location of a library is 1 / n, where n is the number of libraries loaded.